A scammer has stolen our PEPT account

Yesterday, as I do everyday, I check my accounts and do some trading of digital assets.
While I went to check my PEPT account I got an error message from Keychain indicating that a transaction request failed because account credentials were no longer authorized.
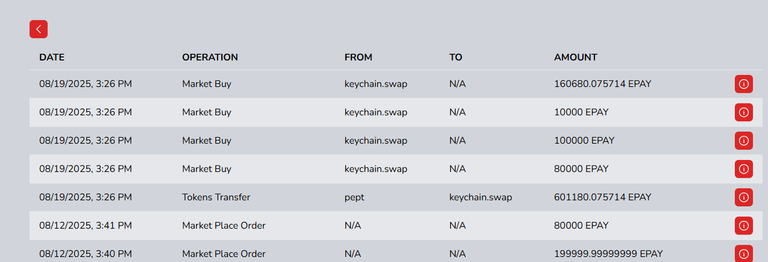
Within a few minutes I noticed that ePay tokens were being dumped at market and thus realized that the account was taken over by a hacker.
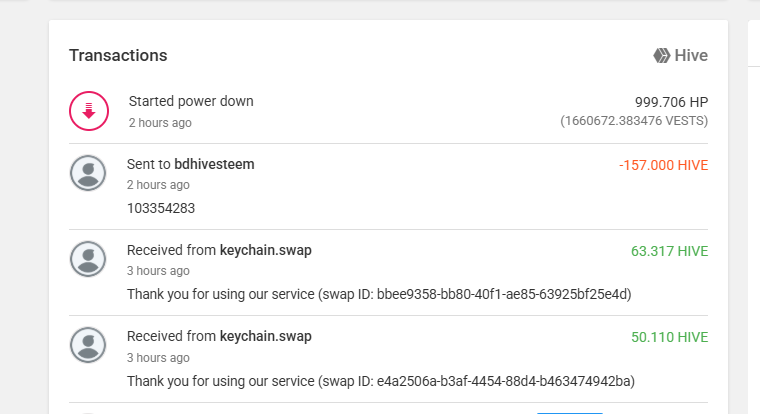
I checked my Hive wallet and saw that keychain.swap and bdhivesteem accounts were used to move stolen funds from Hive to binance.
This is most disturbing because I am well aware of protecting my credentials. I use Roboform password manager, Google Drive and local drive on my desktop PC and laptop. I am not aware of any application where I provided my credentials except keychain app.
Now What?
I have to decide how much time and effort I commit to moving forward on Hive.
First, I have to look at account recovery protection. Turns out, that I was not fast enough in implementing an account recovery tool. So account recovery protection is the first priority.
Next priority is to meditate on why I want to continue with building PEPT on Hive.
Also, since I am a fan of problem solving and this is a #TooFuckeh problem that is not unique to me, I have been chatting in Discord about adding checks and balances to detect unusual account activity.
I am really sadden by how we implement technology in a way that can be so dismissive of small transactions or unusual account activity.
It is clear to me that Binance is a popular blockchain for scammers to transfer stolen funds from Hive. I do not have a Binance account. I only use Hive blockchain. I am learning that the account @bdhivesteem is used to conduct crimes. Most transaction are legit. However, there needs to be some kind of pause placed on a transaction when moving Hive away from Hive blockchain.
Time for me to take a pause from this depressing system. My trust level for Hive is not very high at the moment. I need to see some proactive method or technique applied in the system before I invest more time and money in a business operation on Hive blockchain.
Another crossroad to decided if I should continue building on Hive.
If you have any thoughts and suggestion relating to this event, please do not hesitate to share.
May Positive pepEntropy be with you all.
If this is true, this is very alarming!
Posted using The BBH Project
I don't know for a fact that the keychain file backed up on Google Drive was the hacker's entry. In any case, corrective action was taken.
I can't think of any app I tried that managed to fool me into giving up my PEPT key(s).
I don't know why the PEPT account was the target or why I was a target.
I do know there is still a scammer(s) out there looking to steal Hive and send it to a Binance wallet.
Thanks you for the suggesting and support in Hive discord.
Simply having the pept.json file compromised on google docs would not be enough to gain access to the funds since the keys in the keychain file are encrypted. Therefore an attacker would also need to know the master password, however, if the master password was weak or the computer is compromised by a keylogger, the attacker could obtain both the file and the password, leading to a complete compromise of the account.
Another possibility is that an attacker got the encrypted keys on google docs, and then brute forced the master. Sounds a little bit far fetched, but depending on the length of the master password I suppose it could be possible.
Or a more likely possibility is that someone broke into your house, got onto your computer and did the transfers, maybe a stalker or someone you know or might have seen you on hive?
For the record, I didn't store keys inside a Google doc.
I found a backup txt file and the keychain kc file on my Google drive.
Out of curiosity, when credentials are exchanged between keychain app, or any apps, and a user, is there some server session cookies at play? If so, could a server session cookie be highjacked?
Nope, there are no server session cookies involved when credentials are exchanged between a user and a keychain application. These apps are designed to be secure, client-side storage vaults. Keychain is an encrypted database stored locally on your device. When you save a password, the app encrypts it using keys derived from your device's hardware and your passcode. This makes the data incredibly difficult to access without physical access to the device and the correct password or biometric authentication (like Face ID). When an app needs to access a credential, it requests it from the keychain. The operating system handles the entire process locally without sending the data to a server.
Thank you very much for that explanation.
Much appreciated.
!PIMP
!LOLZ
!SLOTHBUZZ
lolztoken.com
I still wonder what she saw in him.
Credit: reddit
@coininstant, I sent you an $LOLZ on behalf of fjworld
(2/10)
Farm LOLZ tokens when you Delegate Hive or Hive Tokens.
Click to delegate: 10 - 20 - 50 - 100 HP
What you mention is very worrying.
!ALIVE
!PIZZA
$PIZZA slices delivered:
@edgerik(1/15) tipped @fjworld
Come get MOONed!